Do you run a company or business that uses the cloud to store sensitive information about your customers?
If so, then you will need to be SOC 2 compliant. Up until 2014, you would have only needed to be SOC 1 compliant, but no things have changed when it comes to storing sensitive customer data.
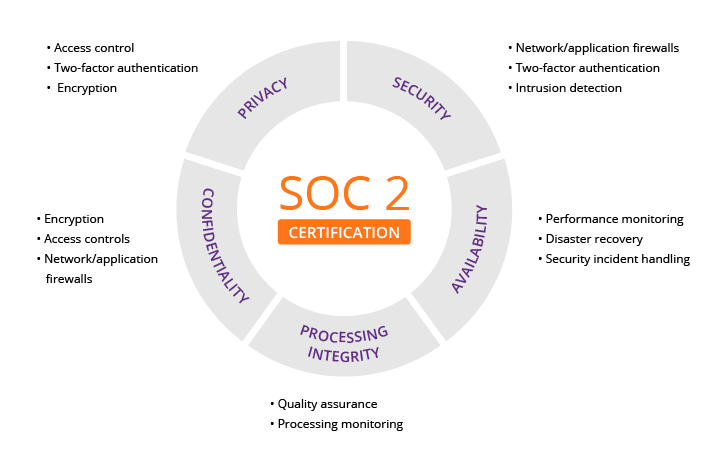
SOC 2 is simply a technical audit and it requires your company to comply with strict policies and procedures regarding the security, integrity, confidentiality, and availability of customer data stored in the cloud. Today, it is a necessity for several different types of organizations.
Here are three things that you will want to know in regards to SOC 2 Compliance:
Have Alerts In Place
Whenever there is a security threat, you need to have a proper alarm system in place so your are alerted to it. This way, if there is any attempted unauthorized access to your customer data, you can respond and take appropriate action.
Examples of security threats that SOC 2 requires you to have alerts set up for include anything dealing with failed login accesses, exposure of data and configurations, or file transfer activities.
Use Audit Trials
Equally as important as being alerted to a security attack is knowing how to respond to it as well. But how can you respond properly without knowing the true root cause between the attack.
This is where SOC 2 audit trials come in. They can tell you multiple details about the attack include who it was, where they came from, and how they managed to breach your security protocols. This way, you can make a more informed decision on how you will respond.
An audit trial specifically will give you insight into the source, the full scope of the attack, any unauthorized modifications that were made into your data, and which system component were modified as well.
Monitor For Unknown Activity
Just as you want to carefully monitor for any known malicious threats, you’ll also want to monitor for threats that are unknown as well.
The best way to accomplish this will be to baseline normal activity in your cloud environment. This way, recognizing any abnormal activity will be made much easier.
SOC 2 compliance means you need to monitor for any unusual system activity and unauthorized changes made to your system’s configuration. It’s for this reason that monitoring for any kind of malicious threats, known or unknown is absolutely vital and should not be ignored.
Staying SOC 2 Compliant
In conclusion, SOC 2 compliance is all about your business or organization having certain procedures in place to ensure that your cloud infrastructure remains secure over the long term.
Not only will staying compliant with SOC 2 ensure that your customer information is kept safe, it will also help you to build a relationship based on trust with each of your customers as well.
………..
 2018 ·
2018 ·
Leave a Reply